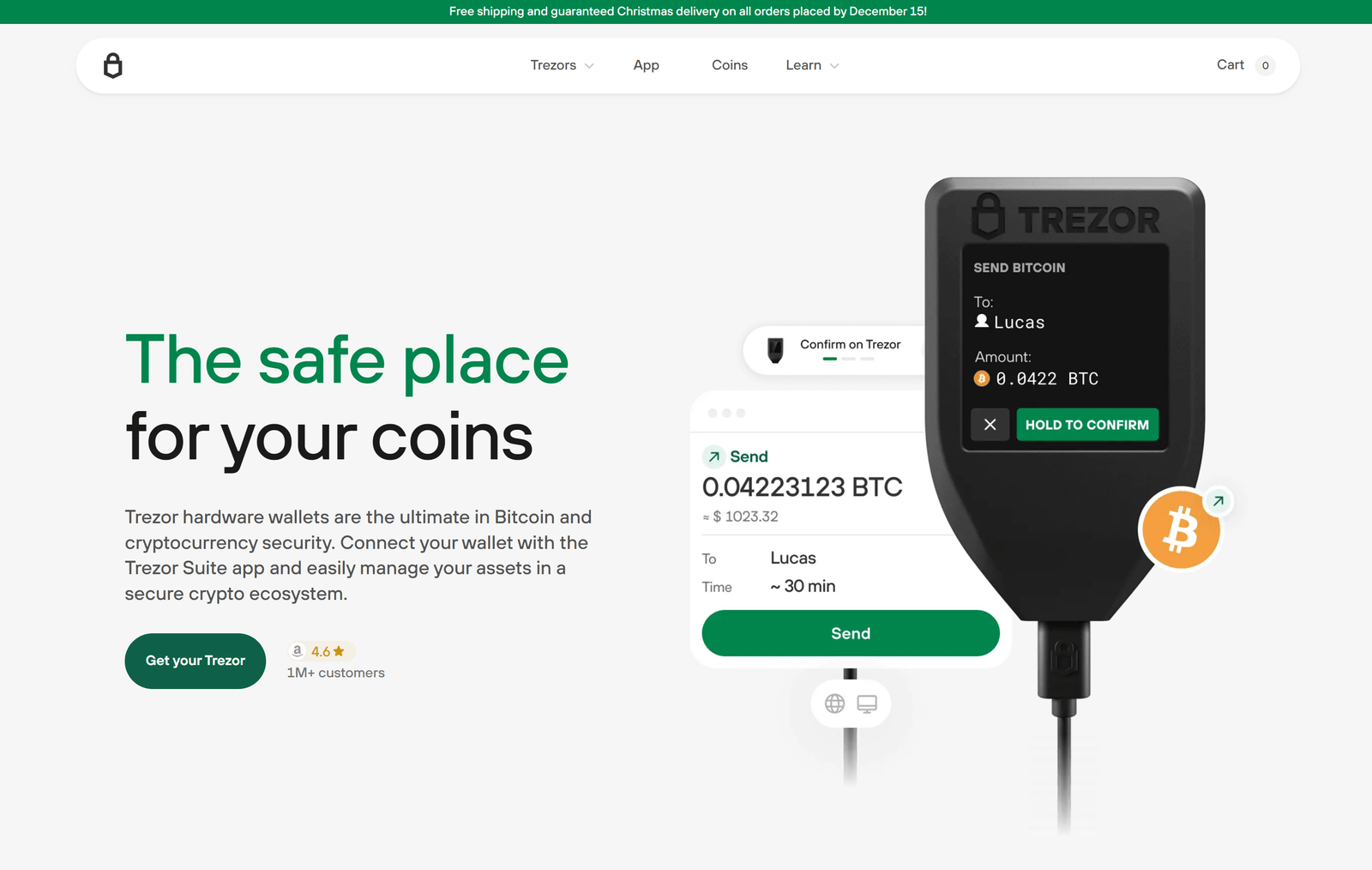
Trezor Bridge: The Essential Link for Secure Crypto Management
In the dynamic realm of cryptocurrency, where security and accessibility intertwine, Trezor Bridge emerges as a pivotal tool for users of Trezor hardware wallets. Developed by SatoshiLabs, this lightweight software serves as a seamless conduit between your Trezor device and web-based interfaces, ensuring secure and efficient management of digital assets. Its role is indispensable for anyone seeking to safeguard their cryptocurrencies while navigating the complexities of modern blockchain interactions.
What is Trezor Bridge?
Trezor Bridge is a sophisticated background application designed to facilitate encrypted communication between your Trezor hardware wallet and supported web browsers or applications, such as Trezor Suite. Unlike outdated browser extensions, which often posed security risks, Trezor Bridge operates as a local HTTP server, translating browser requests into USB commands that your Trezor device can process. This architecture ensures that your private keys remain securely confined to the hardware wallet, never exposed to online vulnerabilities.
Why Trezor Bridge Matters
The significance of Trezor Bridge lies in its ability to bridge the gap between hardware and software, enabling a host of critical functions. It facilitates real-time wallet detection, allowing browsers like Chrome, Firefox, or Brave to recognize your Trezor device instantly upon connection. This eliminates the need for manual configuration, streamlining tasks such as checking balances, authorizing transactions, or updating firmware. Moreover, Trezor Bridge supports advanced features like passphrase-protected hidden wallets and third-party integrations with platforms like MetaMask or Exodus, enhancing its versatility.
Security is paramount in cryptocurrency management, and Trezor Bridge excels in this domain. By maintaining encrypted, local communication, it mitigates risks associated with phishing attacks or malicious extensions. Each transaction or action requires physical confirmation on your Trezor device, ensuring that sensitive operations remain offline and secure. This robust security model makes Trezor Bridge an essential component for both novice and seasoned crypto enthusiasts.
Installation and Compatibility
Installing Trezor Bridge is a straightforward process. Users can download the software from the official Trezor website (trezor.io/start), selecting the appropriate version for their operating system—Windows, macOS, or Linux. Once installed, it runs unobtrusively in the background, automatically detecting your Trezor Model One or Model T upon connection. For optimal performance, users should ensure their browser is up-to-date and uninstall any deprecated Trezor-related extensions to avoid conflicts.
Troubleshooting and Best Practices
While Trezor Bridge is designed for reliability, occasional issues may arise, such as browser detection failures or firewall conflicts. These can typically be resolved by reinstalling the software, updating firmware, or whitelisting Trezor Bridge in antivirus settings. For enhanced privacy, users can pair Trezor Bridge with privacy-focused browsers like Brave or employ a VPN to mask their IP address during setup.
Conclusion
Trezor Bridge is more than a mere utility; it is the backbone of secure and seamless cryptocurrency management. By enabling encrypted communication, automatic device detection, and compatibility across major platforms, it empowers users to manage their digital assets with confidence. Whether you're sending Bitcoin, exploring DeFi, or securing NFTs, Trezor Bridge ensures your Trezor wallet operates at its full potential, safeguarding your financial sovereignty in an ever-evolving digital landscape.
Made in Typedream